VNF vs CNF Introduction
In the fast-evolving world of telecommunications and cloud computing, understanding the difference between VNF (Virtualized Network Function) and CNF (Cloud-Native Network Function) has become crucial. As networks shift from hardware-based infrastructure to software-defined, virtualized environments, both VNFs and CNFs define how modern networks are built, deployed, and scaled.
Telecommunication operators, cloud service providers, and enterprise architects now face a key decision: continue with VNFs or migrate toward CNFs? The right choice depends on scalability, agility, cost efficiency, and 5G readiness.
This article offers a comprehensive comparison of VNF vs CNF, exploring their architectures, benefits, challenges, and migration paths. By the end, you’ll understand both the technical and strategic implications that will shape the future of your network design.
What Is a VNF (Virtualized Network Function)?
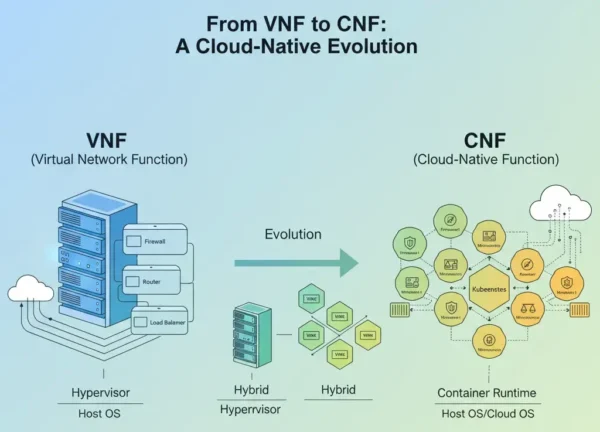
A Virtualized Network Function (VNF) is a software-based version of a traditional network function—such as a router, firewall, or load balancer—that runs on virtual machines (VMs) instead of dedicated hardware. VNFs are part of the Network Functions Virtualization (NFV) architecture, standardized by ETSI (European Telecommunications Standards Institute).
- Runs on VM-based virtualization platforms like VMware, KVM, or OpenStack.
- Uses NFV-MANO (Management and Orchestration) framework for orchestration.
- Reduces dependency on proprietary network hardware.
- Improves CAPEX and OPEX efficiency for service providers.
- Provides enhanced security and isolation via VMs.
According to A10 Networks’ VNF guide, VNFs virtualize key network services like routers and firewalls using commercial off-the-shelf servers. This innovation dramatically accelerated service launches and reduced hardware investments for telecom operators.
What Is a CNF (Cloud-Native Network Function)?
A Cloud-Native Network Function (CNF) represents the next generation of virtualized network functions. Unlike VNFs that depend on VMs, CNFs are designed for containerized, microservices-based environments orchestrated by Kubernetes or similar platforms.
As Zenarmor explains, CNFs are built with cloud-native principles that empower efficiency, agility, and automation:
- Containerization: Each network function runs inside portable, lightweight containers.
- Microservices architecture: Functions are modular and independently deployable.
- Automation: CNFs integrate into DevOps pipelines for continuous delivery (CI/CD).
- Horizontal scalability: Scale up or down instantly with changing traffic loads.
- Resilience: CNFs can self-heal and automatically redeploy across clusters.
In essence, while VNFs virtualize network functions on virtual machines, CNFs fully embrace the cloud-native ecosystem—delivering superior flexibility, automation, and performance.
Why the Shift from VNF to CNF?
The transition from VNFs to CNFs is not just technical; it represents a strategic transformation in the telecom and cloud landscape. The growing demand for agility, automation, and scalability drives this evolution.
According to Red Hat’s comparison of VNF vs CNF, the shift is accelerated by the following factors:
- Operational Efficiency: CNFs deploy faster and consume fewer resources than VNFs.
- Automation: CNFs are built for DevOps, supporting automated scaling and updates.
- 5G & Edge Compatibility: Lightweight container-based deployment suits edge networks.
- Cost Optimization: Reduced overhead and better resource utilization.
- Continuous Innovation: Enables frequent, automated updates and experimentation.
This movement is a major part of the broader Telco Cloud Transformation—a modernization trend that aligns with 5G, edge computing, and AI-driven orchestration strategies.
From PNFs to VNFs to CNFs: The Evolution
To appreciate the rise of CNFs, we must first understand where it all started.
- Physical Network Functions (PNFs): Traditional network functions running on proprietary hardware—rigid, expensive, and hard to scale.
- Virtualized Network Functions (VNFs): Software-based, running on VMs, offering flexibility and cost reduction but limited scalability.
- Cloud-Native Network Functions (CNFs): Microservices-based, running on containers, delivering automation, agility, and cloud scalability.
This progression mirrors the industry’s move toward network softwarization, cloud-native infrastructure, and service agility—foundations for the next-generation digital telco ecosystem.
Scope of This Guide
This in-depth article will help you understand:
- The architectural differences between VNF and CNF.
- The advantages and disadvantages of each.
- How to migrate from VNFs to CNFs successfully.
- The role of 5G, edge computing, and AI in driving CNF adoption.
- Best practices and future trends in telco cloud transformation.
Who Should Read This?
This article is ideal for:
- Telecom engineers and network architects modernizing infrastructure.
- Cloud developers and Kubernetes engineers deploying network workloads.
- Enterprise IT strategists planning cloud-native transformation.
- Project managers overseeing telco and 5G modernization initiatives.
For additional business-focused insights, check out our internal post on adaptability in modern business, exploring how organizations evolve through agility and innovation.
Key Takeaways of Part 1
- VNF: Software-defined functions deployed in VMs—best for legacy or hybrid environments.
- CNF: Containerized, microservices-based, cloud-native functions ideal for 5G and edge networks.
- The industry is rapidly shifting from VNFs to CNFs for better agility, scalability, and automation.
Next: Part 2 — Technical Architecture and Key Differences, where we’ll dive deeper into how VNFs and CNFs are deployed, orchestrated, and optimized in real-world environments.
Part 2: Technical Architecture and Key Differences Between VNF and CNF
Understanding the architectural differences between VNF and CNF is critical to making informed infrastructure and deployment decisions. Both serve the same goal — to virtualize network functions — but the underlying design principles and deployment methodologies vary significantly.
VNF Architecture: Virtual Machines and NFV Stack
VNFs are built to operate within a virtual machine-based environment. They are part of the ETSI NFV architecture, which defines how traditional network appliances are virtualized and managed. The typical architecture consists of the following key layers:
- Virtual Network Function (VNF): The actual software instance providing the network service (e.g., firewall, router, DPI).
- Virtual Infrastructure Manager (VIM): Manages compute, storage, and network resources, commonly via OpenStack or VMware vSphere.
- VNF Manager (VNFM): Handles the lifecycle management of VNFs — including deployment, scaling, and updates.
- NFV Orchestrator (NFVO): Oversees overall orchestration and coordination across multiple VNFs and services.
This architecture enables service providers to deploy network functions as virtual machines on commercial off-the-shelf (COTS) hardware. However, since each VNF runs inside its own virtual machine, the approach introduces some performance and scalability challenges — particularly at large scale or under high traffic loads.
For instance, VNF-based workloads rely heavily on the hypervisor layer, resulting in higher latency and resource overhead. This limits the agility required for next-generation applications like 5G, IoT, and real-time analytics.
CNF Architecture: Containers and Microservices
CNFs, on the other hand, are built on cloud-native principles and deployed as containers instead of virtual machines. This allows them to leverage container orchestration platforms such as Kubernetes and OpenShift for automated deployment and management.
The key elements of a CNF architecture include:
- Containerized Network Functions: Each network function runs as an isolated container — smaller, faster, and more portable than VMs.
- Microservices-based Design: Functions are decomposed into modular services that communicate via APIs.
- Service Mesh: A dedicated control layer (e.g., Istio) manages service-to-service communication, load balancing, and security.
- Kubernetes Orchestration: Automates container deployment, scaling, and health monitoring across clusters.
- CI/CD Integration: CNFs are developed using DevOps pipelines that enable continuous delivery and version control.
Unlike VNFs, CNFs are designed to be stateless wherever possible. This enables rapid scaling and resilience — if a CNF fails, a new instance is automatically spawned elsewhere in the cluster. The result is improved uptime, automation, and operational flexibility.
For a practical overview of cloud-native design patterns and the benefits of CNF orchestration, refer to the internal post on leading through change, which discusses adaptive strategies in network transformation.
Deployment Model: Virtualization vs Containerization
At the heart of the VNF vs CNF debate lies the difference in deployment methodology:
| Aspect | VNF (Virtualized Network Function) | CNF (Cloud-Native Network Function) |
|---|---|---|
| Infrastructure | Runs on Virtual Machines (VMs) managed by a hypervisor. | Runs inside lightweight containers managed by Kubernetes. |
| Orchestration Layer | NFV-MANO framework (VIM, VNFM, NFVO). | Kubernetes and container orchestration platforms. |
| Resource Efficiency | Higher resource usage due to VM overhead. | More efficient; containers share the host OS kernel. |
| Scalability | Vertical scaling — requires additional VMs. | Horizontal scaling — faster container replication. |
| Resilience | Dependent on VM recovery and orchestration tools. | Automatic recovery through container orchestration. |
| Update Mechanism | Manual updates; downtime possible. | Rolling updates and CI/CD pipelines reduce downtime. |
This clear contrast shows why CNFs have become the preferred model for modern 5G and edge network deployments. They deliver superior automation and efficiency, aligning perfectly with DevOps and cloud-native principles.
Performance and Latency
Performance is one of the biggest differentiators between VNFs and CNFs. Because VNFs rely on hypervisors and virtual machines, they suffer from additional abstraction layers that introduce latency. CNFs eliminate much of this overhead by running directly on the host OS kernel.
For example:
- VNF Latency: Typically higher due to VM isolation and virtual NIC drivers.
- CNF Latency: Lower latency and faster packet forwarding thanks to kernel-level networking and DPDK (Data Plane Development Kit) integration.
Furthermore, CNFs enable fine-grained scaling at the container level. If a specific microservice becomes overloaded, Kubernetes can replicate only that component — minimizing waste and improving responsiveness.
Lifecycle Management and Automation
Managing VNFs requires orchestration systems like Open Source MANO or vendor-specific NFV-MANO implementations. These frameworks manage the deployment, scaling, and configuration of virtual machines. However, they often lack the flexibility and speed of modern container orchestration.
CNFs, in contrast, integrate with CI/CD pipelines and Infrastructure as Code (IaC) tools. This enables:
- Automated deployment and rollback of network functions.
- Policy-driven scaling and configuration.
- Self-healing networks that respond dynamically to failures.
- Version-controlled infrastructure management.
These characteristics make CNFs more compatible with agile workflows and continuous innovation cycles. For example, a telecom operator can deploy a new 5G network slice or update a network service with zero downtime — something that’s difficult to achieve using traditional VNFs.
Security Architecture Considerations
Security in VNFs is closely tied to VM isolation — each virtual machine provides a strong boundary between workloads. CNFs rely on container isolation, which, while lightweight, introduces shared kernel dependencies. To mitigate risks, CNF environments use:
- Service Mesh Policies to enforce zero-trust communication.
- Pod Security Policies (PSP) and runtime scanning.
- Network Policies at the Kubernetes layer.
- Container Security Frameworks like Falco and Aqua Security.
Modern CNF deployments also leverage GitOps workflows, which ensure secure, version-controlled infrastructure management — aligning with cloud-native best practices.
Key Takeaways of Part 2
- VNFs rely on virtual machines and NFV-MANO, offering flexibility but with resource overhead.
- CNFs are microservices-based, containerized, and orchestrated with Kubernetes — enabling true cloud-native scalability.
- CNFs outperform VNFs in terms of latency, automation, and continuous delivery.
- While VNFs remain useful in hybrid or transitional networks, the future of telecom infrastructure lies in cloud-native CNFs.
Next: Part 3 — Use Cases, Migration Strategies, and Real-World Examples, where we’ll examine how organizations are transitioning from VNFs to CNFs across 5G, edge, and enterprise networks.
Part 3: Use Cases, Migration Strategies, and Real-World Examples
The transition from Virtual Network Functions (VNF) to Cloud-Native Network Functions (CNF) is not just a technological evolution—it’s a strategic necessity. As networks become increasingly complex and distributed, service providers need greater agility, scalability, and automation. In this section, we explore real-world applications of VNFs and CNFs, the steps to migrate from virtualized to cloud-native infrastructure, and lessons learned from leading telecom and enterprise deployments.
Key Use Cases of VNFs
Despite the growing popularity of CNFs, VNFs remain highly relevant in existing network environments. Many telecom operators and enterprises continue to rely on VNFs to modernize their legacy hardware infrastructure without complete re-architecture.
Here are the primary use cases where VNFs still excel:
- Network Virtualization: VNFs replace hardware-based appliances such as routers, firewalls, and load balancers with software-based equivalents.
- Network Function Consolidation: Operators deploy multiple VNFs on shared infrastructure, optimizing hardware utilization.
- Private Cloud Deployments: Many enterprises prefer VNFs in private cloud setups for regulatory compliance and security control.
- 5G Core Virtualization: VNFs play a transitional role in early-stage 5G deployments before full CNF adoption.
For example, early Network Function Virtualization (NFV) implementations used OpenStack-based VIMs to deliver flexibility and resource efficiency. This laid the groundwork for the cloud-native evolution that followed.
CNF Use Cases: Powering the Cloud-Native Era
CNFs take network virtualization to the next level by aligning with cloud-native design patterns. These functions run in containers and are orchestrated by Kubernetes, enabling rapid scaling, self-healing, and automation. The result is unprecedented agility, ideal for modern 5G, IoT, and edge computing use cases.
Some of the most impactful CNF use cases include:
- 5G Core Networks: CNFs form the foundation of cloud-native 5G core architecture, enabling network slicing, low-latency performance, and on-demand scalability.
- Edge Computing: CNFs can be deployed at edge nodes to process data closer to users, minimizing latency and optimizing bandwidth usage.
- Enterprise SD-WAN Solutions: Cloud-native SD-WAN services leverage containerized functions to manage secure, multi-branch connectivity.
- IoT Infrastructure: CNFs enable rapid onboarding and management of millions of IoT devices with lightweight, scalable services.
- Network Automation Platforms: CNFs integrate seamlessly with DevOps and CI/CD pipelines, facilitating continuous innovation.
As noted by Red Hat’s cloud-native reference architectures, organizations adopting CNFs benefit from faster time-to-market and operational cost reductions through automation and container efficiency.
Comparing VNF and CNF in 5G Networks
The deployment of 5G networks has accelerated the shift from VNFs to CNFs. Traditional VNF models cannot keep pace with the dynamic resource demands and low-latency requirements of 5G applications. CNFs, however, are designed for distributed, elastic, and cloud-native 5G environments.
Here’s how the comparison plays out in a 5G context:
- 5G Core: VNFs provide the initial virtualization of network functions, but CNFs enable complete microservice decomposition and automation.
- Edge Deployments: CNFs run efficiently at the edge, offering faster data processing and lower operational overhead.
- Network Slicing: CNFs make it easier to deploy network slices dynamically using Kubernetes orchestration.
- Continuous Innovation: With CI/CD pipelines, CNFs facilitate frequent updates without downtime, ensuring service continuity.
Telecom operators like AT&T, Verizon, and Deutsche Telekom are already transitioning to CNFs to deliver scalable and resilient 5G networks. These organizations leverage Kubernetes-based orchestration and microservice-driven architectures to meet customer expectations for high-speed, reliable connectivity.
Migration Strategy: From VNF to CNF
Transitioning from VNFs to CNFs is not a “lift-and-shift” operation. It involves a systematic process of rearchitecting network functions to take full advantage of cloud-native principles. Below is a step-by-step guide for successful migration.
1. Assess and Classify VNFs
Begin by identifying which VNFs can be containerized and which require significant reengineering. Legacy VNFs tightly coupled with operating systems or hardware may need to be rewritten for container environments.
2. Modularize Network Functions
Decompose monolithic VNFs into microservices that can be independently deployed, scaled, and updated. This is the foundation for CNF transformation.
3. Choose an Orchestration Platform
Select a container orchestration framework such as Kubernetes or Red Hat OpenShift for automated deployment and lifecycle management. Integrate it with CI/CD pipelines for continuous delivery.
4. Implement Infrastructure as Code (IaC)
Use tools like Terraform and Ansible to manage infrastructure declaratively. This ensures repeatable deployments and version-controlled configurations.
5. Validate Performance and Reliability
Before production rollout, conduct rigorous testing to ensure CNFs meet or exceed the performance benchmarks of VNFs. Incorporate automated testing pipelines into the CI/CD framework.
6. Enable Observability and Monitoring
Adopt observability tools such as Prometheus, Grafana, and ELK stack to monitor performance metrics, detect anomalies, and ensure high reliability in real-time.
Challenges in Migration
Despite the clear advantages, the VNF-to-CNF migration presents several challenges:
- Skill Gap: Network engineers must learn cloud-native technologies and DevOps practices.
- Toolchain Integration: Aligning legacy NFV systems with container ecosystems requires thoughtful integration.
- Security Considerations: CNFs demand new approaches to container isolation and runtime protection.
- Operational Complexity: Managing hybrid VNF-CNF environments can be demanding until full migration is achieved.
However, organizations can overcome these obstacles by adopting a gradual, hybrid approach—running VNFs and CNFs side by side until workloads are fully modernized. This method minimizes risk while maintaining service continuity.
Real-World Examples of CNF Adoption
Several leading telecom and cloud providers have already adopted CNF architectures to enhance agility and operational efficiency. Let’s explore a few real-world examples:
- AT&T: Transitioned from VNFs to CNFs using Kubernetes to support its 5G core infrastructure. This migration reduced deployment time by 50% and improved service resilience.
- Rakuten Mobile: Pioneered a fully cloud-native mobile network built on CNF principles, achieving near-zero downtime and automated network scaling.
- Verizon: Adopted a hybrid cloud-native model integrating CNFs with OpenShift, enabling real-time orchestration for enterprise and consumer services.
- Orange Group: Uses CNFs to deliver multi-access edge computing (MEC) solutions for low-latency applications such as AR/VR and industrial IoT.
Each of these organizations demonstrates how cloud-native transformation drives agility and competitive differentiation in an era of digital convergence.
For a related perspective on leadership during digital transformation, check out the internal post on leading through change, which discusses strategies for navigating complex technology shifts.
Benefits of Successful Migration
- Improved time-to-market for new network services.
- Reduced operational costs through automation.
- Enhanced scalability for handling dynamic workloads.
- Seamless integration with DevOps pipelines.
- Stronger resilience and fault tolerance in production environments.
The shift from VNF to CNF enables service providers to embrace continuous innovation, reduce vendor lock-in, and deploy network services in minutes rather than weeks.
Summary of Part 3
- VNFs remain valuable in transitional or hybrid architectures.
- CNFs are the future of network automation and 5G scalability.
- A structured migration roadmap minimizes risk and maximizes ROI.
- Organizations worldwide are already achieving measurable benefits through CNF adoption.
Next: In Part 4, we’ll examine the performance, scalability, and security comparison between VNFs and CNFs, and how each impacts modern network operations.
Part 4: Performance, Scalability, and Security Comparison Between VNF and CNF
As network architectures evolve, understanding the trade-offs between VNF (Virtual Network Function) and CNF (Cloud-Native Network Function) performance becomes crucial. These two paradigms differ not only in how they are deployed but also in how they scale, operate, and protect critical data. This section provides a detailed analysis of their performance metrics, scalability mechanisms, and security architectures in modern telecom and enterprise environments.
Performance Overview
Performance in a virtualized or cloud-native environment depends on how efficiently the software interacts with underlying hardware resources. VNFs rely on hypervisors and virtual machines, whereas CNFs leverage containers that share the host kernel, reducing abstraction layers. This results in faster response times, improved throughput, and reduced latency.
According to research from Cloud Native Computing Foundation (CNCF), CNF-based workloads can achieve up to 40% lower latency compared to equivalent VNF deployments when properly tuned with DPDK (Data Plane Development Kit) and SR-IOV. This difference is especially impactful for 5G networks and edge computing applications, where real-time performance is essential.
In addition, you can find insights on AI and Network Transformation to understand how performance optimization ties into AI-driven orchestration within next-generation networks.
Resource Utilization and Efficiency
One of the key performance differentiators between VNFs and CNFs is resource utilization. VNFs consume more CPU, memory, and disk I/O because each function runs in its own virtual machine, complete with a guest operating system. In contrast, CNFs run as lightweight containers, sharing the host OS kernel, which significantly improves efficiency.
- VNFs: Require dedicated virtual machine instances; resource-heavy and slower to scale.
- CNFs: Utilize shared container infrastructure; lightweight and dynamically scalable.
For telecom operators, this difference translates into tangible savings. Deploying CNFs instead of VNFs can reduce infrastructure costs by up to 30% while improving application responsiveness. Furthermore, CNFs can leverage Kubernetes node autoscaling to automatically balance workloads across clusters, maintaining consistent performance during traffic spikes.
Latency and Throughput
Latency remains a major performance metric in network environments. In traditional VNF deployments, the use of hypervisors and virtual network interfaces introduces additional hops, increasing end-to-end packet delay. CNFs, with their containerized architecture, operate much closer to the host kernel, allowing for near-native network performance.
| Metric | VNF | CNF |
|---|---|---|
| Average Latency | 3–5 ms (dependent on hypervisor) | 1–2 ms (optimized for container I/O) |
| Packet Processing Throughput | Moderate – impacted by VM isolation | High – enabled by kernel-level networking (DPDK) |
| Network Stack Efficiency | Moderate | Optimized with SR-IOV and CNI plugins |
By using Container Network Interfaces (CNI) such as Calico or Cilium, CNFs achieve near bare-metal performance — a critical requirement for 5G and edge computing workloads.
Scalability and Elasticity
When it comes to scaling network services, CNFs outperform VNFs by a wide margin. VNFs typically require provisioning additional virtual machines to handle increased load, a process that can take minutes. CNFs, however, support near-instantaneous horizontal scaling through Kubernetes, which can launch new containers in seconds.
Scaling in VNFs:
- Vertical scaling (add more resources to a VM).
- Slower provisioning times due to hypervisor dependency.
- Manual orchestration or NFV-MANO systems required.
Scaling in CNFs:
- Horizontal scaling (add more containers automatically).
- Self-healing and auto-scaling through Kubernetes policies.
- Integration with CI/CD pipelines for dynamic updates.
For organizations running 5G core networks, scalability is essential to support varying traffic loads. CNFs make it possible to instantly scale network slices based on real-time demand, while VNFs often struggle with elasticity due to rigid VM-based infrastructure.
Reliability and Fault Tolerance
Reliability is another crucial aspect of network operations. CNFs, designed for distributed architectures, excel in fault isolation and recovery. If one container or microservice fails, Kubernetes automatically redeploys it elsewhere without impacting the rest of the system.
VNFs, however, are less resilient. A failure in the virtual machine or hypervisor can cause entire services to become unavailable until recovery scripts or manual intervention restore them.
- VNF Fault Recovery: Dependent on hypervisor and VNF Manager; slower response.
- CNF Fault Recovery: Automated through Kubernetes self-healing and replica sets.
For additional insights on automation and reliability, see how to build effective teams — which explores resilient architectures and operational collaboration in digital ecosystems.
Security Considerations
Security is a shared responsibility between infrastructure and application layers, and both VNFs and CNFs approach it differently. VNFs depend heavily on VM isolation — each virtual machine runs its own OS, providing a strong security boundary. CNFs, on the other hand, rely on container isolation, which is more lightweight but potentially more exposed due to a shared kernel.
VNF Security Characteristics:
- Isolation via hypervisor and VM boundaries.
- Traditional patch management and OS hardening.
- Secure boot and image integrity verification.
CNF Security Characteristics:
- Micro-segmentation with Kubernetes network policies.
- Runtime container security (Aqua Security, Falco).
- Zero-trust communication through service mesh layers like Istio.
- Immutable infrastructure and version-controlled deployments (GitOps).
To maintain parity with VNF-level security, CNF environments use Pod Security Policies (PSP), runtime scanning, and continuous monitoring. Additionally, Kubernetes admission controllers help enforce compliance and prevent unauthorized container actions.
Operational Efficiency and Automation
Operational automation is where CNFs truly outshine VNFs. With Infrastructure as Code (IaC), CI/CD pipelines, and declarative management, CNFs enable full automation of deployment, scaling, and monitoring. VNFs, in contrast, often rely on manual configuration or vendor-proprietary management tools.
- CNFs integrate seamlessly with GitOps workflows, ensuring consistent configurations.
- Kubernetes offers built-in observability through metrics, logging, and alerting.
- Container orchestration enables policy-driven scaling and rollback.
These advantages translate directly into faster innovation cycles and lower operational costs — core benefits of adopting cloud-native network architectures.
Key Takeaways of Part 4
- Performance: CNFs achieve near-native speeds with lower latency and better throughput.
- Scalability: Kubernetes-driven horizontal scaling provides elasticity unmatched by VNFs.
- Security: CNFs introduce advanced container-based security but require diligent configuration and runtime protection.
- Reliability: Automated self-healing mechanisms ensure higher uptime in CNF-based environments.
Next: In Part 5, we’ll conclude with an in-depth comparison summary, FAQs from users, and final recommendations for organizations deciding between VNF vs CNF in their digital transformation journey.
Conclusion: The Future of Network Virtualization — From VNF to CNF and Beyond
The debate of VNF vs CNF is not about competition—it’s about evolution. VNFs laid the groundwork for modern virtualized networks, enabling operators to move away from proprietary hardware and toward software-defined infrastructure. CNFs take this transformation further, embracing cloud-native architectures to deliver unmatched scalability, agility, and automation.
In an era dominated by 5G, edge computing, and network slicing, the transition from VNF to CNF represents a strategic necessity rather than a choice. CNFs enable telecom operators and enterprises to:
- Accelerate service rollout and deployment cycles.
- Automate network management and resource optimization.
- Ensure better resilience and faster recovery through container orchestration.
- Integrate seamlessly with DevOps pipelines for continuous innovation.
As noted by the Cloud Native Computing Foundation (CNCF), Kubernetes and container technologies are now the backbone of modern network infrastructure. Organizations that embrace CNFs position themselves for a more dynamic, scalable, and intelligent networking future.
VNF vs CNF: The Key Takeaway
While VNFs are still widely deployed and remain relevant in hybrid infrastructures, the long-term trend is clear—CNFs are the foundation of next-generation telecom and enterprise networks. The move toward cloud-native transformation aligns with broader digital initiatives such as automation, observability, and AI-driven orchestration.
For example, operators adopting CNFs alongside 5G enterprise transformation strategies can drastically improve flexibility and network performance at lower costs. Similarly, teams working with network automation tools can leverage CNFs to implement intelligent scaling and auto-healing capabilities.
Ultimately, agility, automation, and resilience are what distinguish CNFs from VNFs. The cloud-native era is not only about technology but about reimagining how networks are built, managed, and evolved.
FAQs About VNF vs CNF
1. What is the main difference between a VNF and a CNF?
The primary difference lies in their deployment architecture. VNFs run on virtual machines and rely on hypervisors for isolation, while CNFs run in containers and are managed through Kubernetes for orchestration. CNFs are more scalable, lightweight, and cloud-native by design.
2. Can VNFs and CNFs coexist in the same network?
Yes, hybrid environments are common. Many telecom operators deploy VNFs and CNFs side by side, especially during network modernization phases. This coexistence allows gradual migration without service disruption.
3. What are the benefits of moving from VNFs to CNFs?
Transitioning to CNFs enables faster scalability, better automation, and reduced resource overhead. It also aligns network operations with DevOps and CI/CD methodologies, supporting continuous innovation.
4. Do CNFs replace NFV?
CNFs extend the principles of NFV into the cloud-native world. Instead of replacing NFV, CNFs represent its evolution—adopting containers, microservices, and dynamic orchestration to achieve the same goals more efficiently.
5. How do CNFs impact 5G deployment?
CNFs are central to 5G architecture. They power 5G Core Network Functions by enabling network slicing, automation, and ultra-low latency. With CNFs, 5G networks can dynamically allocate resources to meet diverse user and enterprise requirements.
6. What tools are used to manage CNFs?
Common CNF orchestration and management tools include Kubernetes, Helm, OpenShift, and ONAP (Open Network Automation Platform). These platforms handle deployment, scaling, and lifecycle management.
7. Is migrating from VNF to CNF complex?
Migration involves challenges, especially for legacy VNFs that were not designed for containerization. However, adopting a phased migration strategy—starting with non-critical VNFs—helps reduce risk. Utilizing automation and CI/CD pipelines simplifies the process.
8. Are CNFs more secure than VNFs?
Both VNFs and CNFs can be secure when properly managed. However, CNFs offer enhanced security through isolation at the container level, immutability principles, and dynamic policy enforcement via service meshes like Istio or Linkerd.
Practical Recommendations for Network Operators and IT Teams
1. Conduct a Cloud-Native Readiness Assessment
Before transitioning from VNF to CNF, assess your organization’s infrastructure, DevOps maturity, and automation capabilities. Identify which network functions can be containerized with minimal refactoring.
2. Adopt a Hybrid Strategy
Operate VNFs and CNFs concurrently during migration. This hybrid model enables gradual adoption while maintaining service continuity. Integrating both via orchestration layers such as ONAP provides seamless interoperability.
3. Invest in Kubernetes Expertise
Kubernetes is the cornerstone of CNF orchestration. Train your DevOps and network teams in Kubernetes, Helm charts, and cloud-native CI/CD pipelines. Consider certifications such as CKA (Certified Kubernetes Administrator) or CKS (Certified Kubernetes Security Specialist).
4. Prioritize Observability and Automation
Use observability tools to monitor CNF performance in real time. Leverage automation frameworks for scaling, fault recovery, and security updates. This ensures optimal performance and uptime across distributed networks.
5. Collaborate with Ecosystem Partners
Leverage partnerships with open-source communities, cloud providers, and telecom vendors to access cutting-edge CNF frameworks. Explore Open Networking Foundation initiatives for guidance on standards and interoperability.
6. Plan for Continuous Evolution
As technology advances, CNFs will evolve further toward serverless networking and AI-driven orchestration. Prepare for iterative improvements by maintaining flexibility in your network design and architecture.
Final Thoughts
The journey from VNF to CNF marks a decisive shift toward cloud-native, software-defined networking. Organizations that embrace this transformation gain a competitive edge through speed, scalability, and resilience. As the telecom and enterprise worlds converge around 5G and automation, CNFs are no longer an option—they’re the foundation of the next-generation network.
For continued insights on digital transformation, read our related guides on cloud-native network architecture and software-defined networking trends.
In conclusion, understanding and implementing CNFs isn’t just a technical upgrade—it’s a strategic move toward agility, automation, and long-term innovation.